Network Support Services
ISoft Solutions ensures 24/7 fast , personalized network support services to minimize downtime, safeguarding your business from financial losses and productivity disruptions.
Network Support Services of ISoft Solutions
When your company’s network is down, your business loses money and productivity. You need a reliable network support team on call, to bring your systems online. When you are being partner with ISoft Solutions, you get fast, personalized network support 24/7 hours.
Network Support of ISoft Solutions
- Network Support of ISoft Solutions Comprehensive assistance to ensure optimal network performance and security.
- Viruses: Malicious software designed to damage or disrupt systems.
- Hacking: Unauthorized access to computer systems for stealing or manipulating data.
- Power outages: Interruptions in the electrical supply that can disrupt network operations.
- Failed or faulty software patches: Updates that do not install correctly or cause issues, leading to potential vulnerabilities.
- Natural disasters: Events such as floods, earthquakes, or storms that can damage network infrastructure.
- Changes in the configuration of devices: Modifications that can lead to connectivity or security issues.
- Mismanagement of devices: Poor handling or maintenance of network devices, causing inefficiencies or failures.
- Human error: Mistakes made by individuals that can compromise network integrity.
- Firewall: Security system that monitors and controls incoming and outgoing network traffic.
- IPSEC Point-to-Point VPN: Secure network communication between two specific locations.
- SSH VPN Service: Encrypted VPN service using the Secure Shell protocol for secure access.
- SSL VPN Service: Virtual private network that uses Secure Sockets Layer to provide secure remote access.
- Microsoft Terminal Server, Remote Desktop Services: Services allowing users to access a remote computer or server.
- Custom Secured Access Applications: Tailored applications designed to provide secure access to network resources.

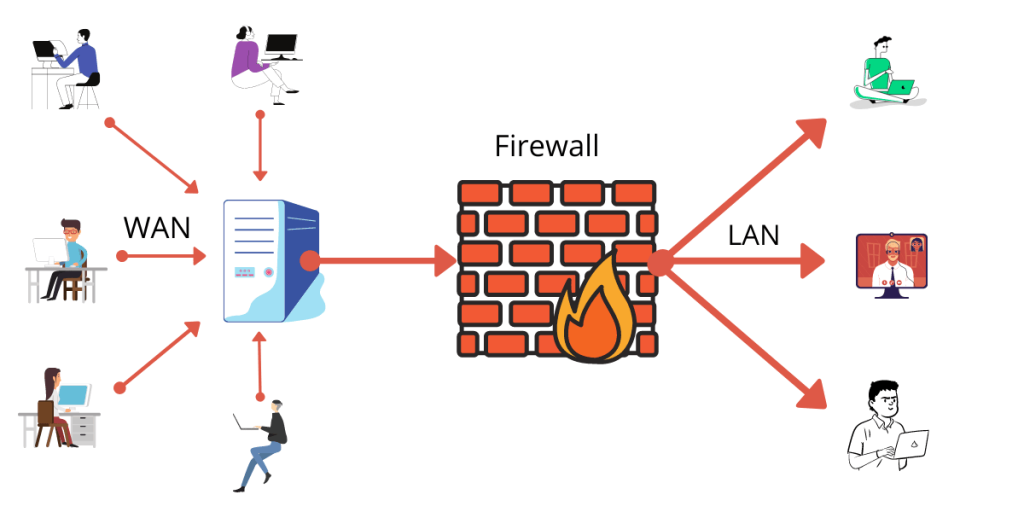
Firewall
- Next-Generation Endpoint Protection
- Business Continuity Solutions (Backup/Disaster Recovery)
- Spam Filtering
- 24/7 Network/Server/Workstation Monitoring
- Patch Management
- Network Documentation
- Dark Web Monitoring
- Phishing Simulations
- Security & Awareness Training
Cloud Services
- Cloud-Based Applications (e.g., Office 365)
- Cloud Infrastructure
- Core Business Apps
- Cloud Integrations and Security Tools
"Partners who keep trust in Us"







